Dell has been hit with 2 security issues the past few days. I wanted to quickly summarize my findings from an external network perspective:
1. Laptops come pre-installed with a root certificate
The root certificate is issued by eDellRoot. Initially, the story mentioned just one certificate but it quickly became clear that there was a 2nd certificate that can be found on live web servers using Shodan with the search query:
ssl:eDellRoot
At the moment, the search returns 28 results that are located mostly in the US with a few in Switzerland, Canada, Singapore and Malaysia:
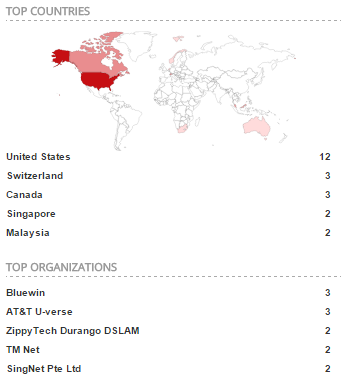
Even though there are very few results, at least one of them has turned out to be a control system. This isn't a big surprise since there are millions of control systems connected to the Internet but it's a good reminder that the Internet has much more than just web servers.
Dell has issued a statement explaining the existence of the root certificate and released a tool/ instructions on how to remove it.
2. Webserver runs on port 7779 that provides unauthenticated access to the Dell service tag
http://www.theregister.co.uk/2015/11/25/dellbackdoorpart_two/
There are ~12,800 webservers on the Internet running on port 7779. Out of those, roughly ~2,300 are running software that looks like it's from a Dell computer:

I wrote a quick script to grab the service tags from those IPs and was able to collect ~1,000 service tags. The other 1,300 devices didn't respond in time or otherwise errored out when trying to query the information. Of course, much of the threat is the ability to execute Javascript to gather the information from localhost but I wanted to get a sense of how many are Internet-connected. I've also added port 7779 to Shodan so it will be possible to keep track of how the issue gets resolved over time.