Analyzing Post-WannaCry SMB Exposure
It's been a month since the WannaCry ransomware attack wrecked havoc across Windows networks via SMB and I'd like to take a moment to review where we're at today. Here are some numbers to kick things off:
- 2,306,820 SMB services available on the Internet at the moment
- 42% allow Guest access
- 96% support SMBv1
- 16,206 have DoublePulsar
- 91,081 are vulnerable to MS17-010
DoublePulsar and MS17-010
Initially, we observed around 100,000 services on the Internet affected by DoublePulsar. That number slowly declined over time but then took a dramatic drop once WannaCry was released.
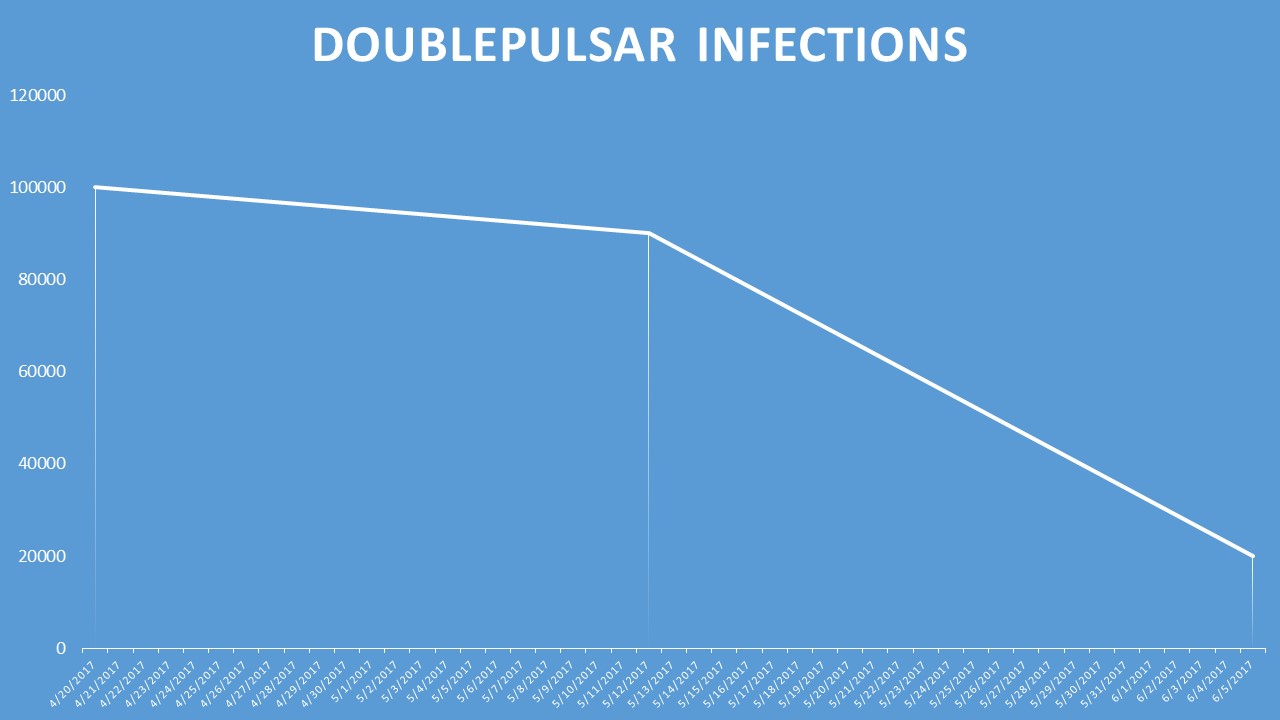
The DoublePulsar infections are continuously going down which indicates that people aren't using the publicly-available code released by the Shadow Brokers against Internet-accessible SMB. Theoretically, all Windows devices running SMB should be patched by now and therefor no longer vulnerable to the issues in MS17-010. If that were the case it would explain the lack of DoublePulsar propagation. However, there are still at least 91,081 devices vulnerable to MS17-010 which means that there remains a significant exposure of vulnerable SMB services on the Internet.
Understanding SMB Deployments
SMB version 1 is more than 20+ years old and widely considered to be deprecated, inefficient and insecure. There are also many newer versions available of the SMB protocol that address the short-comings of the initial SMB version. At the moment, the vast majority (96%) of SMB services on the Internet support SMBv1 - only 4% require SMBv2 in order to connect.
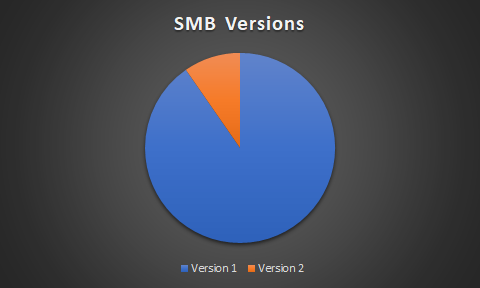
That's not a huge surprise as SMBv1 support is enabled by default on most products and many popular tools expect SMBv1 to be running.
In terms of guest access, 42% allow anonymous access to their SMB service:
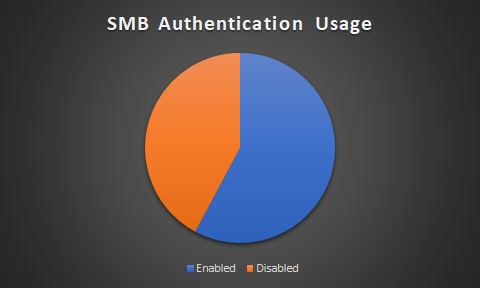
The chart only tells half the story, though. It turns out that more than 90% of them are running Samba. Basically, almost all of the instances of SMB on the Internet that allow guest access are running Samba - i.e. not the Windows SMB service. By default, neither SMB service allows guest access. I speculated that there might be a packaged release of Samba somewhere that may allow guest access by default but once I looked at the distribution of results the issue became clear:
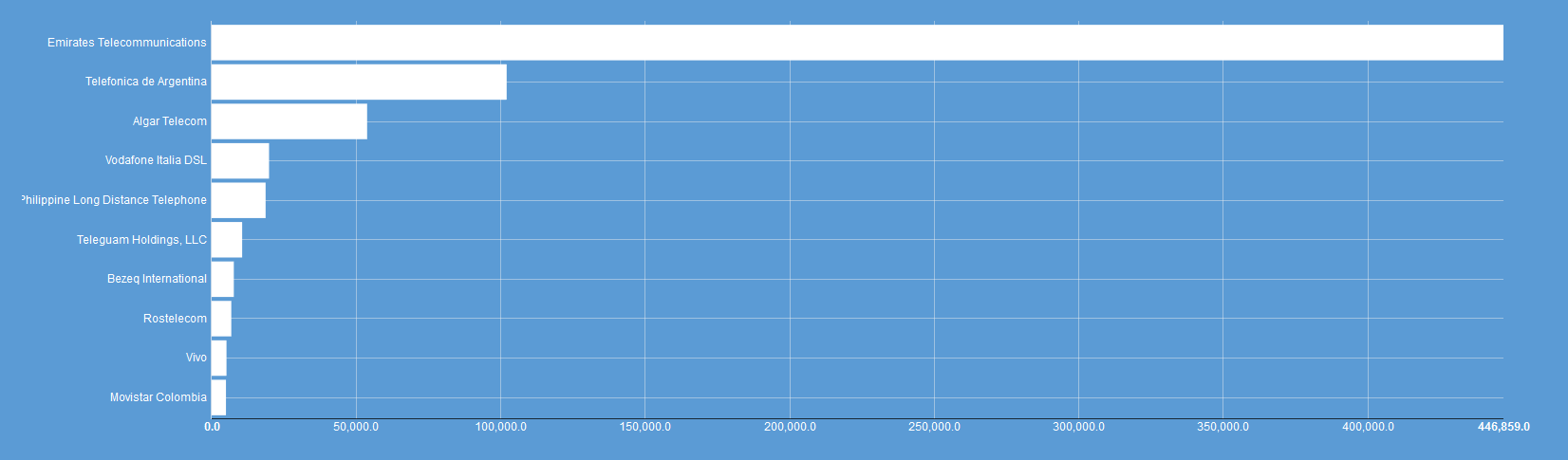
Of the Samba instances that allow guests 50% are located on the network of Etisalat. Even though there are many systems on the Internet that expose guest access the numbers show the exposure is largely caused by a single Internet provider.
Finally, while there was an initial drop in total SMB exposure on the Internet after DoublePulsar/ WannaCry we've since started seeing a steady increase again.
PS: Shodan has been keeping track of SMB on the Internet since January, 2013.