Deep Dive: Malware Hunter
There are many ways to track command & control servers from bad guys but they often rely on looking for indicators in the service metadata (ex. certificate information). Around a decade ago we developed a novel technique to proactively find the infrastructure: Malware Hunter. Malware Hunter finds command & control (C2) servers by pretending to be an infected Windows XP computer and sending the C2 handshake to every IP on the Internet. In other words, it tells every IP on the Internet that it's just been infected and is ready to join the botnet that the IP is managing. If the IP welcomes Malware Hunter as a new bot then we know that the IP is actually running a C2 and we add a malware tag to the banner. One of the interesting differences with this type of approach is that we're often able to identify C2s on residential networks before they go into "production" because we're proactively finding them on the Internet. Note that Malware Hunter doesn't send any malicious requests as it's pretending to be infected - all of its activity is benign.
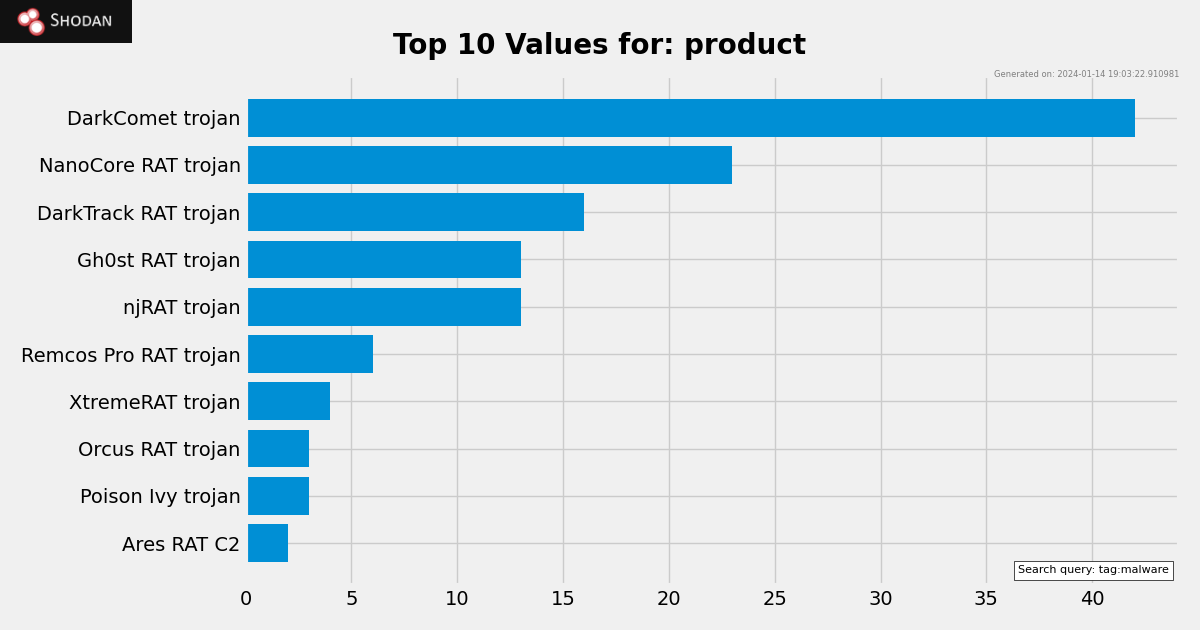
The information is accessible for free to everybody with a Shodan account. Here is a breakdown of the protocols that Malware Hunter currently identifies:
You can use the API or CLI to get a list of the IPs:
shodan stats --facets ip:1000 tag:malware | sed -e '1d' -e 's/ .*//' | sort
Help Wanted
Is there a new C2 protocol or malware family that you would like Shodan to track? Please send us an email with any of the following:
- Traffic data: a PCAP or technical documentation that tells us how the callback to the C2 looks like.
- Code: if there is already code available for interacting with the C2 then that is immensely helpful.
- Research: blog posts, articles or any technical documentation that describes the C2 protocol.
Many of the current identifications are based on help we've received from users or threat intelligence companies over the years and we're always looking to expand the active tracking of C2s.