I've started collecting screenshots for a few services, most notably VNC, and something stuck out at me:
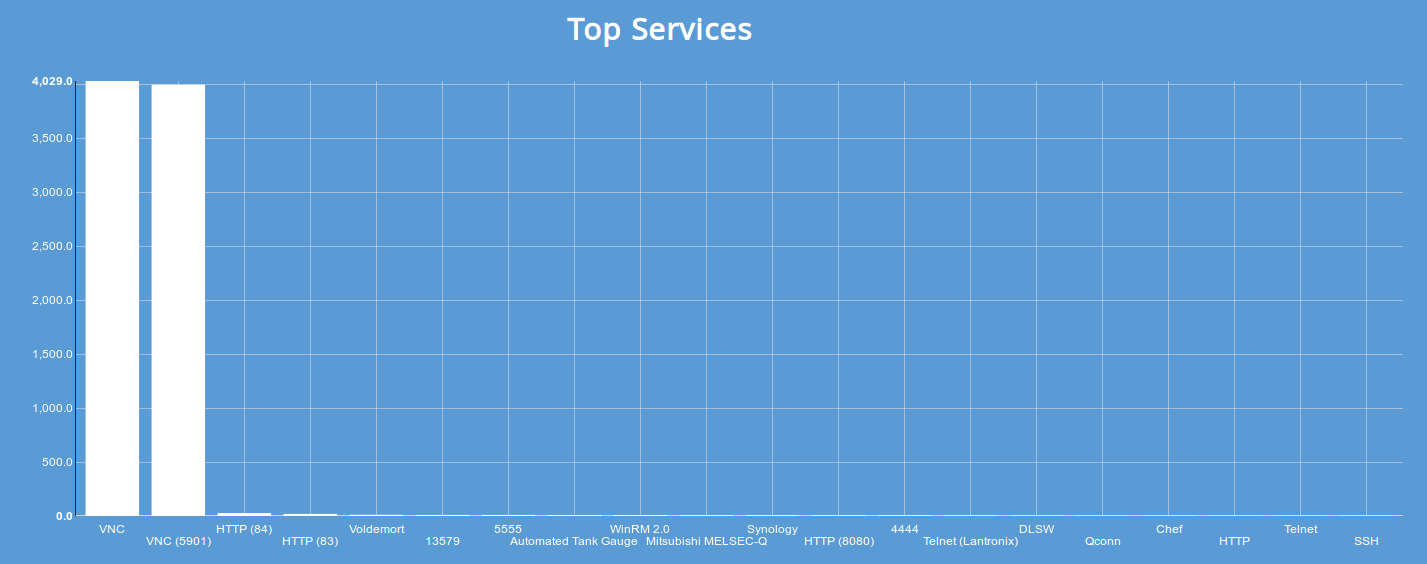
The top 5 ports where VNC is running with authentication disabled are:
- 5900 (default port): 4,029
- 5901: 3,995
- 84: 25
- 83: 14
- 13579: 7
Out of ~8,000 results, 50% of the results came from services that were operating VNC on a non-standard port. It's not unusual to see common services running on different ports, but that was a surprising amount. My guess is that a lot of people change the default port thinking that it will hide their service. Because Shodan scans for 250+ different ports however, there's a small chance that Shodan will discover it anyways. And for a lot of the popular protocols, Shodan actually also crawls for one-off ports (thank you to @Viss for that idea).
I've seen this sort of behavior in other services as well, this isn't limited to VNC. If you've read my previous blog posts this might sound familiar to you. In fact, I observed much of the same when looking at SSH. For SSH, the choice of ports is a bit wider but in general people don't work well as random number generators.
Furthermore, this sort of behavior can be observed across the industries. For example, you might know that Shodan crawls the Internet for industrial control systems (ICS). One of the most popular protocols in ICS is called Modbus that runs on port 502. At the moment, there are about 17,000 devices listening to Modbus on the default port. It turns out there are also 700 devices listening on port 503, again a one-off sort of situation.

If you're looking to hide your service putting it on a different port is a temporary band-aid at best and a false sense of security more than anything.