Back in December when I revamped the SSH banner and started collecting the fingerprint I noticed an odd behavior. It turns out that a few SSH keys are used a lot more than once. For example, the following SSH fingerprint can be found on more than 250,000 devices!
dc:14:de:8e:d7:c1:15:43:23:82:25:81:d2:59:e8:c0
And there are many more fingerprints that are also duplicated, which you can check out yourself using the following Python code:
import shodan
api = shodan.Shodan(YOUR_API_KEY)
# Get the top 1,000 duplicated SSH fingerprints
results = api.count('port:22', facets=[('ssh.fingerprint', 1000)])
for facet in results['facets']['ssh.fingerprint']:
print '%s --> %s' % (facet['value'], facet['count'])
Going back to the fingerprint mentioned above, when you plug that into Shodan the picture becomes somewhat clearer:
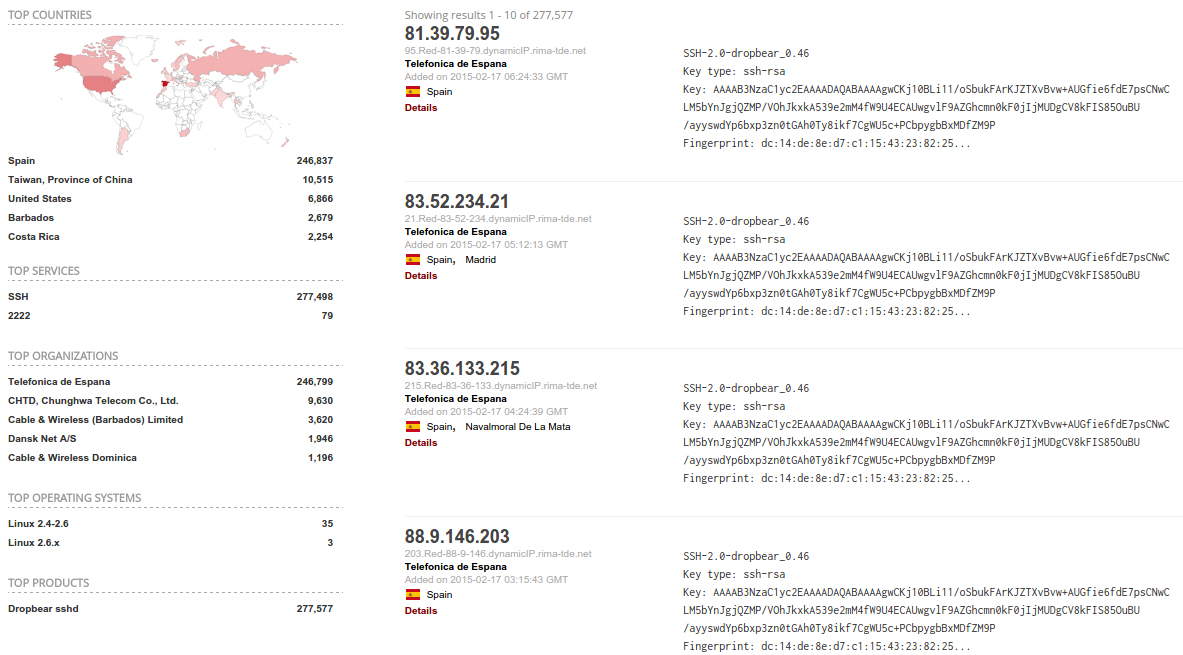
It looks like all devices with the fingerprint are Dropbear SSH instances that have been deployed by Telefonica de Espana. It appears that some of their networking equipment comes setup with SSH by default, and the manufacturer decided to re-use the same operating system image across all devices.
The next duplicated fingerprint on the list comes in at around 200,000 devices, followed by another one used by 150,000 devices. By analyzing the facets it's easy to get a picture of systemic issues that plague both hardware manufacturers as well as ISPs/ hosting providers. I've uploaded a list of unique fingerprints and their counts to the following Gist location:
https://gist.github.com/achillean/07f7f1e6b0e6e113a33c
Feel free to download the CSV and start analyzing the duplicated fingerprints because there are a lot of them. I wouldn't be surprised if you'd uncover interesting security issues by analyzing why these things are misconfigured.