I've made some improvements to the way SSL is indexed and added 2 new filters:
- ssl
Search all SSL-related information that Shodan collects.
Example: ssl:Google - has_ssl
Boolean filter to only show results/ banners that contain SSL information.
There was also a bug in how the SSL serial numbers were indexed so after that got patched I kept an eye on the results. To do so I used the command-line interface and faceted on the ssl.cert.serial property to get a list of the most popular SSL serial numbers:
The top 5 SSL serial numbers are:
- 15264109253415148488
- 17803741903183845083
- 0
- 40564819207326832829647457238321
- 295
I wasn't sure what to expect so lets take a look at what the most popular SSL serial on the Internet is used by:
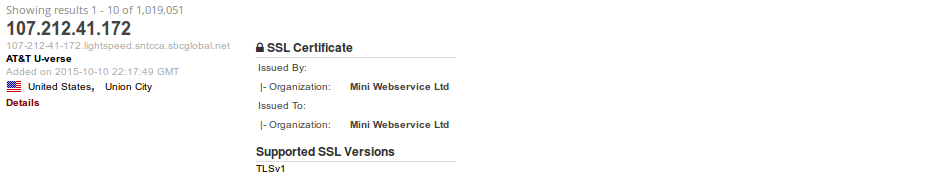
There are more than a million devices that use the serial number 15264109253415148488 and none of them return a banner. They're all self-signed certificates that are running a service on port 443 but otherwise aren't responding to HTTP requests. Hmmm, ok well what about the 2nd most popular serial number?
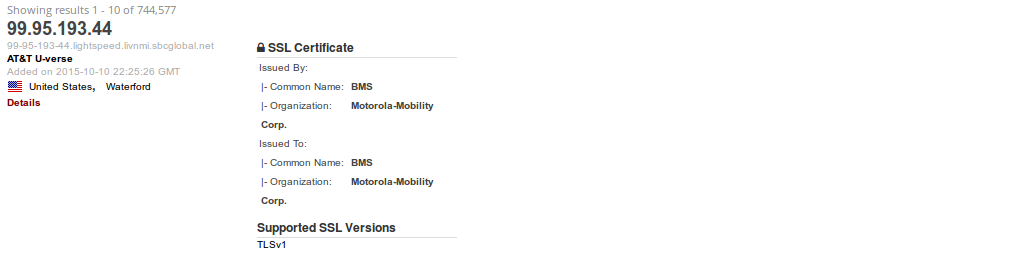
Once again a huge amount of devices are responding on port 443 and not providing any banners but this time for Motorola Mobility devices. In both instances the devices are located on AT&T's network, and based on the netblock ownership the IPs are being used for U-verse. I started searching for more information about these certificates and eventually found an answer:
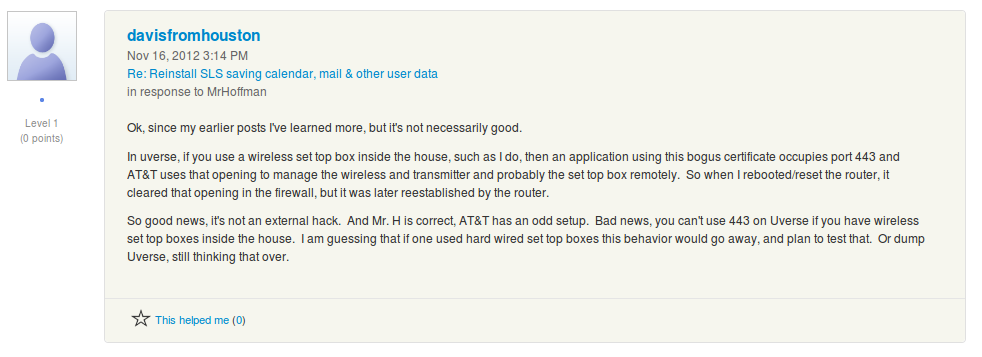
Apparently, AT&T is running a service on port 443 to manage their wireless set top boxes. I don't have any way to verify those claims but they seem plausible. If nothing else it's now very easy to see how many of AT&T's users purchased their wireless Internet package (~2 million households).
