I wanted to revisit the results of a few posts last year on how to track website defacements and see how things have changed since then. In case you're wondering how this data is collected, I've created a video that shows in real-time the commands I used to generate the data:
Here's the Top 10 Website Defacers as of January 2016:
- GHoST61: 51
- Kadimoun: 39
- AnonCoders: 35
- r00t-x: 31
- Shor7cut: 28
- Owner Dzz: 27
- Toxic Phantom FROM BANGLADESH BLACK HAT HACKERS: 27
- TechnicaL: 21
- virus3033: 21
- Yuba: 17
GHoST61 also topped the ranking last year and remains at the top at the moment. Other familiar names are: r00t-x (moved down 1 rank), TechnicaL (moved down 2 ranks) and virus3033 (moved down 2 ranks). This means that 4 of out of the previous top 10 are still around, while the other 6 weren't listed before.
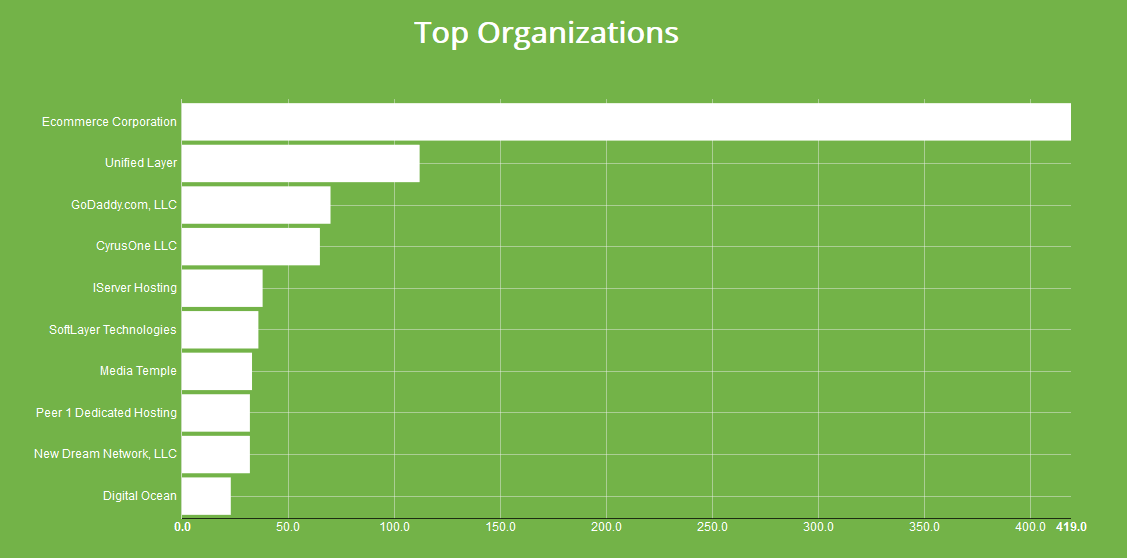
In terms of organizations containing defaced websites, the Ecommerce Corporation remains the most affected by far. At this point it seems a given that Ecommerce will have the worst ranking so lets look at the other organisations on the list. The full ranking is:
- Ecommerce Corporation
- Unified Layer (+1)
- GoDaddy (-1)
- CyrusOne
- iServer Hosting
- SoftLayer Technologies
- Media Temple (-1)
- Peer1 Dedicated Hosting (-4)
- New Dream Network
- Digital Ocean
The top 3 have remained the same, though GoDaddy and Unified Layer switched spots. New entries on the list are: CyrusOne, iServer Hosting, SoftLayer, New Dream Network and Digital Ocean. At this point it's clear that there are a few hosting providers with on-going problems and it doesn't look like they've made any impactful changes to reduce the number of compromised websites.
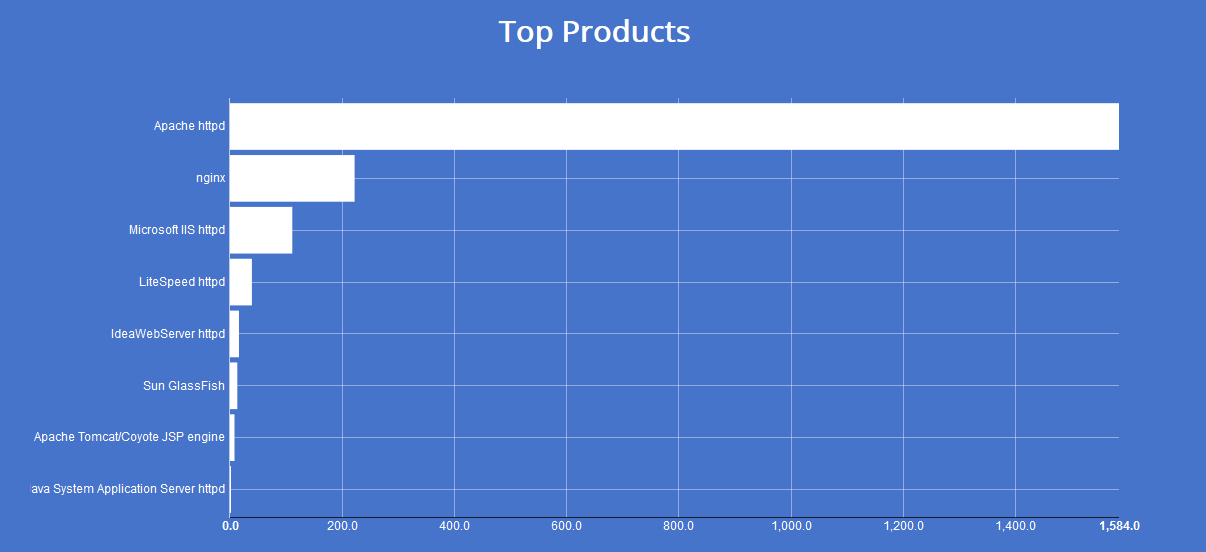
In terms of products, the vast majority of affected websites were running Apache:
I'm planning on periodically revisiting this subject to see how things change over time, especially with regards to the newly-listed organisations!
PS: Credit to @Viss for the dramatic hacker background image at the top.